Why Audit Trails & Access Logs Are Crucial for GDPR Accountability in Document Sharing
The GDPR's Accountability principle isn't just about being compliant; it's about proving you are. When it comes to sharing documents containing personal data – think contracts, HR files, client information – demonstrating responsible handling is paramount. This is where robust audit trails and access logs become indispensable tools, not just technical features.
Simply using email or basic cloud storage often leaves significant gaps in your ability to demonstrate accountability. If a data subject requests information (a DSAR) or a potential breach occurs, can you confidently prove who accessed specific documents, when, and what actions they took? Without detailed logs, the answer is often no, leaving your business vulnerable. (Understanding GDPR fundamentals)
Let's explore why audit trails are crucial for GDPR accountability in document sharing and what constitutes a meaningful log.
GDPR accountability principle
The Accountability principle is a cornerstone of the GDPR. Article 5(2) states that the data controller (your business) is responsible for, and must be able to demonstrate compliance with, the core data protection principles outlined in Article 5(1). This means having records and evidence to show you're handling personal data lawfully, fairly, transparently, and securely.
For document sharing, accountability translates to proving you have implemented appropriate technical and organizational measures to protect the data within those documents throughout their lifecycle, including when accessed by others.
The role of audit trails in demonstrating compliance
Audit trails provide the necessary evidence to meet the accountability requirement. They create a chronological record of events related to document access and handling. A reliable audit trail allows you to:
- Verify Authorized Access: Confirm that only permitted individuals viewed sensitive documents.
- Investigate Incidents: Trace steps leading to a potential breach or unauthorized disclosure.
- Respond to Data Subject Access Requests (DSARs): Provide information on processing activities related to an individual's data contained within documents.
- Support Internal Audits: Review practices and ensure policies are being followed.
- Demonstrate compliance to regulators if required.
Without these logs, proving compliance becomes a matter of assertion rather than documented fact. (See 10 GDPR principles for document handling)
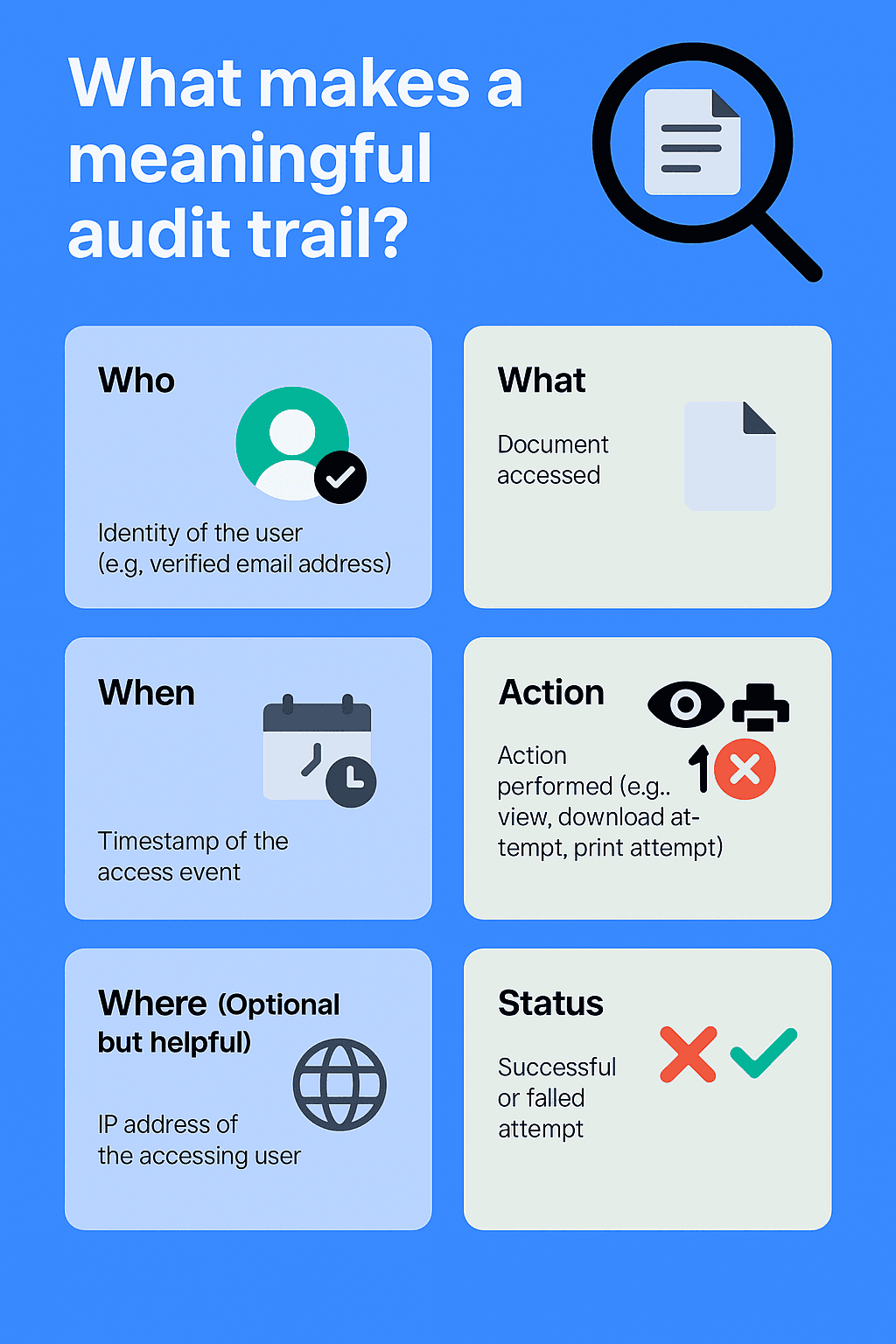
What makes a meaningful audit trail?
Not all logs are created equal. A meaningful audit trail for GDPR accountability in document sharing should capture specific, relevant information for each access event:
- Who: The identity of the user accessing the document (e.g., verified email address).
- What: The specific document that was accessed.
- When: A precise timestamp (date and time) of the access event.
- Action: What action was performed (e.g., view, download attempt (blocked/allowed), print attempt).
- Where (Optional but helpful): IP address of the accessing user (can help identify suspicious activity).
- Status: Whether the access attempt was successful or failed (e.g., due to incorrect password).
This level of detail provides a clear picture of how documents containing personal data are being interacted with.
Why basic logs aren't enough for accountability
Standard tools often fall short. Consider these limitations:
- Email: Provides only a 'sent' record, with no confirmation of receipt, opening, or subsequent actions (forwarding, saving). You lose all visibility once it leaves your outbox.
- Basic Cloud Storage (e.g., public links): May offer simple view counts but often lack user identification (who viewed?), specific action logging (did they try to download?), or reliable timestamps for individual access events. Anonymous access logs are insufficient for accountability.
Imagine needing to prove only authorized HR personnel viewed a sensitive employee contract. An email log can't help, and a basic cloud storage 'view count' doesn't identify who those viewers were. This lack of detail makes demonstrating GDPR compliance impossible.
How detailed logs help meet compliance obligations
Platforms designed for secure document sharing, like Papermark, prioritize granular logging specifically for accountability:
- Breach Investigation: If a breach is suspected, detailed logs instantly show who accessed the compromised document(s) around the time of the incident, significantly speeding up investigation and containment.
- DSAR Responses: When a user requests details about their data processing, logs can confirm if documents containing their data were accessed, by whom, and when, helping fulfill the request accurately.
- Proof of Limited Access: Logs demonstrate that you enforce access controls (like password protection or email verification) and can prove that only authorized parties viewed specific documents.
- Policy Enforcement: Audit trails help verify that internal policies regarding document handling and access are being adhered to. (Need a secure sharing checklist?)
These capabilities directly support the GDPR's accountability principle by providing concrete evidence of data protection practices.
Conclusion: Accountability requires evidence
GDPR accountability is an active requirement, demanding demonstrable proof of compliance. In the context of document sharing, detailed audit trails and access logs are not optional extras; they are fundamental components of a compliant system. Relying on inadequate logs from email or basic cloud storage creates unnecessary risks.
By implementing solutions that provide comprehensive, user-specific logging, you gain the visibility needed to manage access effectively, respond to incidents, fulfill regulatory obligations, and ultimately, build trust by proving your commitment to data protection.
Ready to enhance your GDPR accountability?
Papermark provides detailed, real-time audit trails for every document you share. Track who views your documents, when, and for how long, with features like email verification ensuring you know exactly who is accessing sensitive information.